Security Enhancements in Active IQ Unified Manager 9.9 Part 2: Audit Log Enhancements
It is essential that you have support to monitor your audit log files. With NetApp® Active IQ Unified Manager, we provide such support with our audit log feature that monitors and logs the changes you make to an audit log file. In this second blog in the Active IQ Unified Manager 9.9 series, we discuss the enhancements we have made to the audit log feature to improve and simplify the audit log managment process.
The enhanced audit log scope
In the Active IQ Unified Manager 9.9 release, we expanded the scope of the audit log feature to capture the following actions in the audit log:
- All successful and unsuccessful login attempts
- All logout attempts
- User management actions, such as object creation, modification, and deletion of Performance Service Levels, users, groups, performance policies, alerts, notifications, external authentication details, and HTTPS certificates
- All Active IQ Unified Manager REST API invocations
The new audit log inventory page
We added a new audit logs inventory page to track and display the audit logs file details. You can access the Audit Logs page by selecting General > Audit Log. The inventory page displays the audit log file name, file size, creation date, archive date, file integrity status, and reasons (optional).
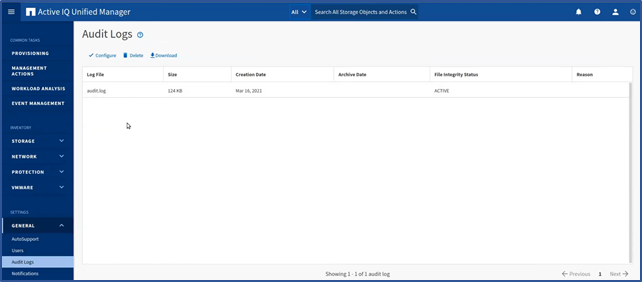
The File Integrity Status attribute captures the status of each audit log file. The attirbute is actively monitored to detect for tampering or deletion of a file and indicates if the audit file log is active, normal (inactive), has been tampered with, or has been manually or rollover deleted. It also applies restrictions that prevent you downloading and deleting certain audit log files.
Configure the audit log properties
You can use the Configure button in the Audit Logs inventory page to configure audit file properties such as maximum file size, total audit log size, audit log retention period in months, and select the Enable Remote Logging option to external servers.
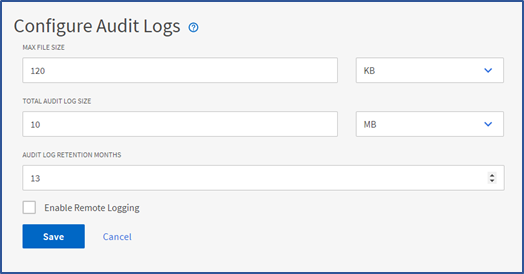
You should note the following features:
- The default MAX FILE SIZE value is 17 MB and the maximum value is 512MB.
- The default time period for AUDIT LOG RETENTION MONTHS is 13 months and the maximum value is 120 months. The system automatically rolls over any file that is older than the value set in this field.
- The default TOTAL AUDIT LOG SIZE value is 100MB and the maximum value is 10GB.
- The roll-over policy is determined by the values in the field AUDIT LOG RETENTION MONTHS, MAX FILE SIZE, and TOTAL AUDIT LOG SIZE.
- When the size of the audit log backup reaches the value in TOTAL AUDIT LOG SIZE, the system deletes the file that was archived first and marks the deleted file as a Rollover Delete.
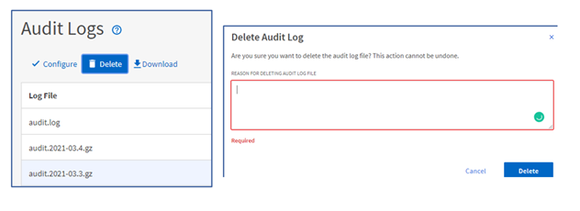
Manually delete audit log files
You now have the option in the audit log inventory page to manually delete audit log files from your system by selecting the DELETE button to delete audit log files listed in the Audit Logs view. If you choose to, you can also provide a reason for the deletion which is added to the REASON column along with your name.
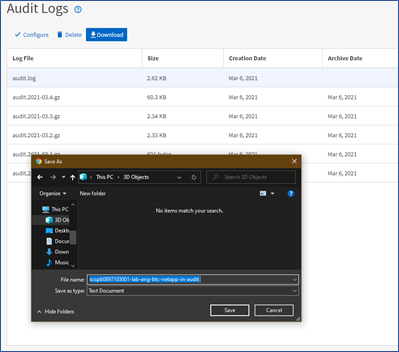
Download audit log files
We have added the option to download audit log files to your system by selecting the DOWNLOAD button on the Audit Logs inventory page. The process downloads the log files as text files and downloads the files marked as NORMAL or TAMPERED in a compressed .gzip format, as you can see in the following sample output.
It’s important to note that when you generate a full AutoSupport bundle, the support bundle includes both archived and active audit log files. But when you generate a light support bundle, it only includes the active audit logs.
Audit log forwarding
In the Active IQ Unified Manager 9.9 release, we have introduced remote log forwarding to a syslog server. To access this support, you first select the Enable Remote Logging checkbox in the Configure Audit Logs dialog box to enable remote logging of audit logs. You then upload the public certificate for the target syslog server by selecting the BROWSE button in the SERVER CA CERTIFICATE field. The certificate should upload in the .pem format, come from the target syslog server, be within expiration, and contain the selected hostname as part of the SAN attribute.
At this point, you can input the appropriate CHARSET, CONNECTION TIMEOUT, and RECONNECTION DELAY in milliseconds. Take care when choosing the FORMAT type and only select the supported IETF(RFC 5424) or BSD(RFC3164) formats. Similarly with the PROTOCOL type, only select the supported TLSv1.2 or TLSv1.3 formats. After you save the configurations, you can view the syslog certificate by selecting View certificate Detail.
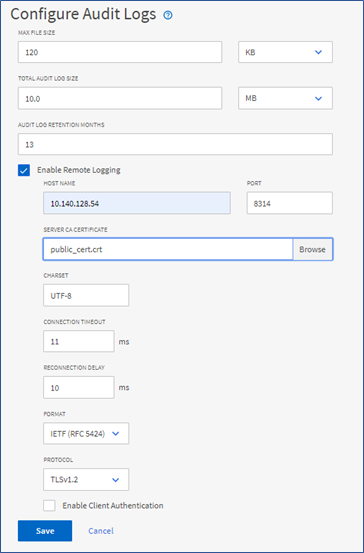
If the target syslog server requires a client certificate-based authentication, simply select the Enable Client Authentication checkbox, download the client authentication certificate and then upload it to the syslog server before saving the audit log configuration.
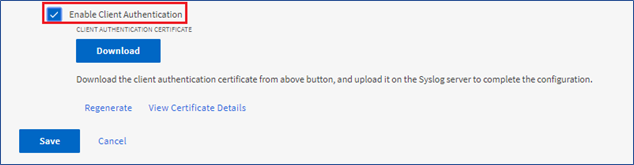
The DOWNLOAD button appears after you select the Enable Client Authentication checkbox. After you select DOWNLOAD, you can select Regenerate to regenerate the certificate. Finally, if you want to view the certificate details, select View Certificate Details.
When you use the Transport Layer Security Mutual Authentication (or peer authentication), Active IQ Unified Manager sends its own certificate when the TCP connections are established. In this scenario, to ensure that you have mutual authentication, follow the pre-requisite setup described in the Administration Guide
Now that you have read about the Active IQ Unified Manager audit log feature enhancements, we hope it entices you to update and try out Active IQ Unified Manager 9.9.
If you would like more information, contact us (ng-aiqum-feedback@netapp.com) and we would be happy to answer your questions.