Building shared infrastructure is a challenge. A typical corporate data center either has dedicated infrastructure for important applications or shared elements that are overengineered to far exceed requirements. Either approach underutilizes resources and wastes budget.
The problem is that it can be difficult to predict how infrastructure components such as servers, networks, and storage will behave as additional load is added. Cloud computing has made understanding all aspects of multi-tenant environments—in which all resources are shared between separate applications, groups, or customers—even more critical.
That’s why NetApp has joined forces with Cisco and VMware to create a complete solution for secure multi-tenancy. This solution has been fully tested in our laboratories, and it has also been deployed by numerous companies. For instance, Tier 3, a leading provider of managed services for small and medium-sized businesses, was able to transform its data centers into shared yet secure clouds that deliver infrastructure as a service (IaaS) and storage as a service (StaaS) while reclaiming 67% of the storage for their virtual server environment and cutting backup time for the entire data center from 24 hours to 1 hour. (See the ExamWorks sidebar for another example.)
Figure 1) Secure multi-tenancy solution components.
In this article, I describe the design principles that serve as the foundation of the joint solution and offer pointers to resources that you can use to guide your cloud deployment.
Four Pillars of Multi-Tenancy
Many companies hesitate to build cloud infrastructure or to contract for cloud services because of fears about security and quality of service. That’s why NetApp, Cisco, and VMware created our secure, multi-tenant cloud architecture. Our design delivers on four pillars of secure multi-tenancy:
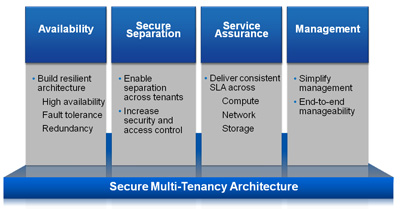
- Availability. If a shared infrastructure fails, it could affect 10, 20, or 50 clients. Therefore the infrastructure that we defined provides built-in redundancy and other mechanisms so that required compute, network, and storage resources remain available in the face of possible failures.
- Secure separation. One tenant must not be able to access another tenant’s virtual machine, network, or storage resources under any circumstance. Each tenant must be securely separated. We’ve implemented security measures in each layer for end-to-end protection.
- Service assurance. Compute, network, and storage performance must be isolated and guaranteed during normal operations as well as when failures have occurred or when certain tenants are generating abnormal loads. This solution sets the class of service as close to the application as possible, maps that value into a policy definition, and makes sure that the policy is applied uniformly across all layers in accordance with the unique qualities of each layer. (This topic was covered in detail in a previous tech OnTap article, “End-to-End Quality of Service.”)
- Management. The ability to rapidly provision, manage, and monitor all resources is essential. Our goal was to simplify management while avoiding locking you in to a particular vendor. We detailed the API integration points at every level and detailed the workflow so that any third application vendor can provide management for the complete environment (if they choose).
Figure 2) Pillars of multi-tenancy.
Comprehensive References
One of the big advantages of the joint solution is that NetApp, Cisco, and VMware have done all the hard work and testing up front. If you tried to create your own solution with similar capabilities, you’d spend hours searching for and working through the best practices of your chosen vendors, and still it would be difficult to be sure that everything would work together to provide end-to-end performance and security.
We’ve created two comprehensive documents that describe this architecture in detail. The design guide explains the mechanisms that support each of the four pillars of multi-tenancy, including why important design decisions were made.
Our deployment guide is a step-by-step cookbook that details every action that is necessary to configure this environment. This guide is divided into two sections; the first describes how to set up the infrastructure, and the second covers how you deploy each tenant once the environment is configured.
Overall, this design emphasizes flexibility. Rather than locking you into rigid hardware limits, it allows you to size a shared infrastructure for your specific needs, from modest to massive, and then scale any dimension independently as necessary.
Cooperative Support
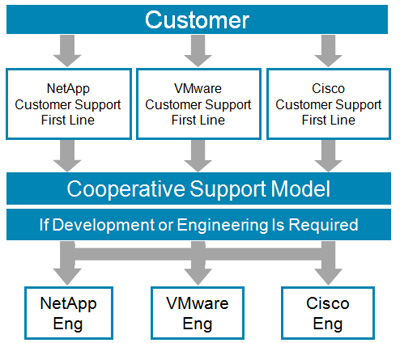
An additional advantage of our secure multi-tenant solution is cooperative support. You can call any of the three support organizations and get help with your entire infrastructure. Our support organizations engage directly with each other, as well as with their engineering organizations. Your problem stays open until it is resolved, whether it relates to servers, networks, storage, or virtualization.
Figure 3) Cooperative support model.