Active IQ Unified Manager Discussions
- Home
- :
- Active IQ and AutoSupport
- :
- Active IQ Unified Manager Discussions
- :
- Re: Can not add or delete AD SVM accounts
Active IQ Unified Manager Discussions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When tying to add or delete an SVM AD account i get the following message.
Failed to get credentials for a domain user who has the ability to remove the Active Directory Account based on the domain Location: Row '1' step 'Delete Active Directory account'.
Solved! See The Solution
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sebastiaan,
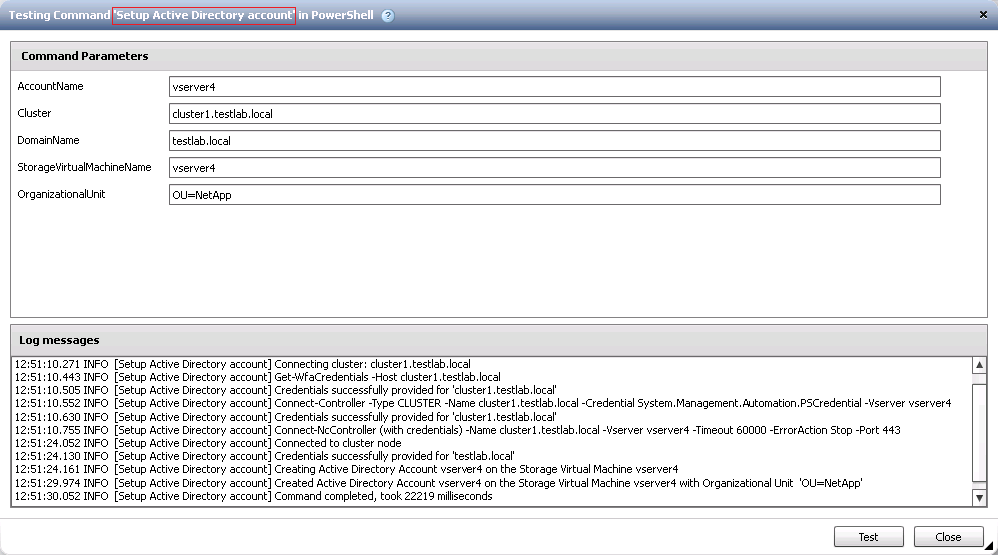
I also test this for you, if you use the WFA certified command "Setup Active Directory Account" it creates the computer object within the security context of the AD service account you've added to WFA and therefore the permissions on the computer object that is created is assigned the delete permissions required for the service account that created it. EG
You can then use the "Delete Active Directory account" command to successfully delete the computer object.
/Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Within the description of that command here is a pre-requisite they mention:
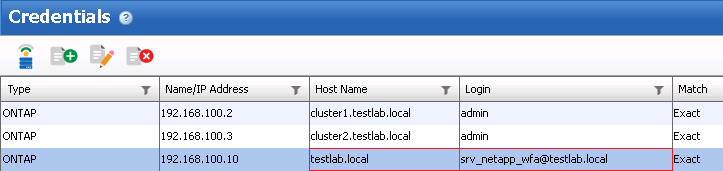
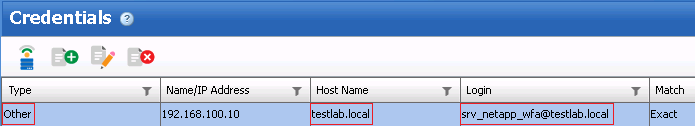
2. WFA credentials should be created for the FQDN of the domain. These credentials need to be of a domain user that has the ability to remove the Active Directory Account configured on the Storage Virtual Machine to the target organizational unit.
See attached screenshot for where to put that credential.
I haven't done this in a while, so the syntax of the username may need to have the domain\user or it may not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The credentials we're created like just like in your screenshot. So i've tried the domain\user syntax but still the same error. The user is able to create and delete accounts in the AD because runnning it from cli works fine.
Isn't there ask for the username/password in the workflow?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also found this error in the wfa.log
Credential Request Rejected for host ''
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sebastian,
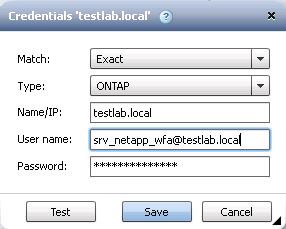
As corey mentioned, there is a prerequisite to add credentials for the domain account. I think this should be entered in UPN (User Principle Name) format. EG:
To verify the UPN from the CLI (assuming directory services tools are installed)
C:\>dsquery user -samid srv_netapp_wfa | dsget user -upn upn srv_netapp_wfa@testlab.local dsget succeeded
In the WFA credentials is should look something like this (Where "hostname" if the domain FQDN and "login" is the AD users UPN)
/Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi i've already tried this and dind't work the. Also must the type be ontap? because it's an account to connect to the AD to create an AD account. I've verified that the upn is usernam@domain.local and it was correct. Have you seen that the WFA log says that the credential request is rejected? it seems that the credentials are not passed to the wfa script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sebastian,
I set this up in a lab for you and think i've found the root cause of the issue (Yes the credential type should be set to "other" not ontap...sorry my bad)
I think the root cause is due to the method and permissions in which the computer account is created.
For example, if you were to use the CLI and the default domain "administrator" account to create the computer:
cluster1::> vserver active-directory create -vserver vserver2 -account-name vserver2 -domain testlab.local -ou OU=NetApp In order to create an Active Directory machine account, you must supply the name and password of a Windows account with sufficient privileges to add computers to the "OU=NetApp" container within the "TESTLAB.LOCAL" domain. Enter the user name: Administrator Enter the password:
C:\>dsquery computer -samid vserver2$
"CN=VSERVER2,OU=NetApp,DC=testlab,DC=local"
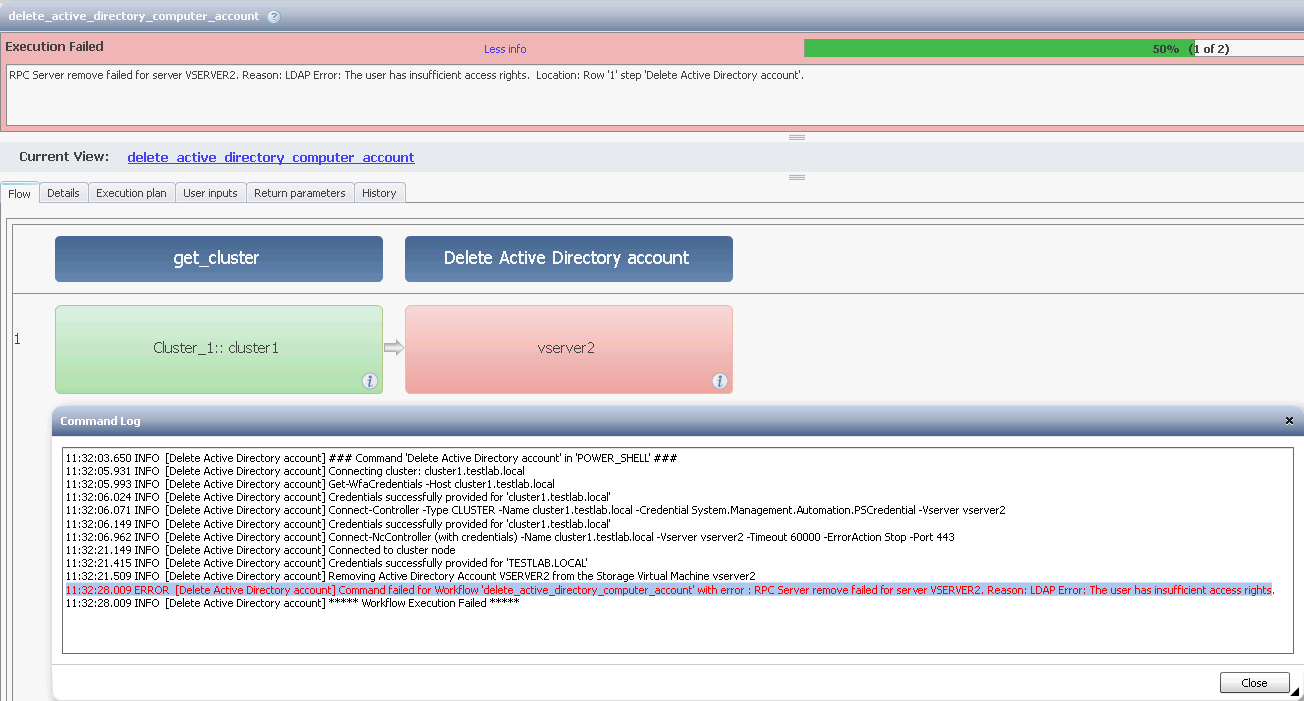
You will get the following error when attempting to use the WFA certified command "Delete Active Directory Account"
The reason for the error is as stated "The user has insufficent access rights". That is because the Domain Administrator account is assigned permissions to delete computer object when it is created (not the AD service account which is being used to attempt to delete it as below):
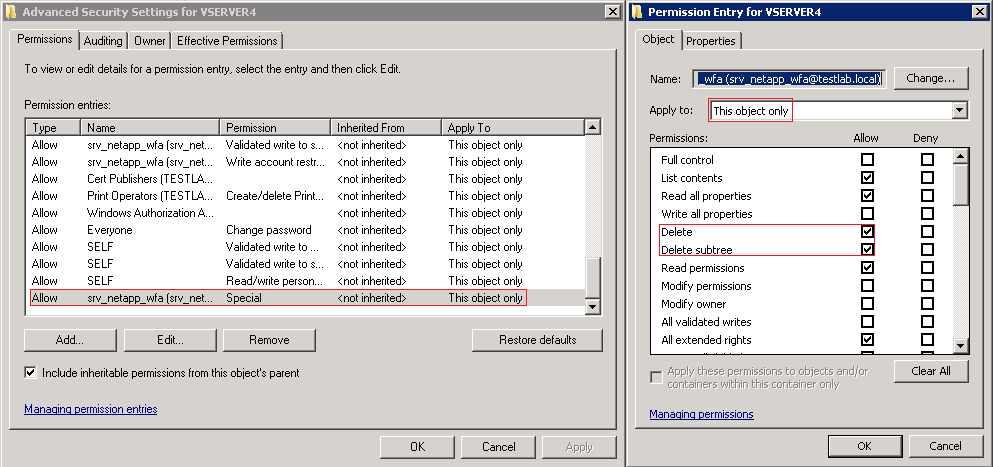
To demonstrate this, if you were to follow the process in the AD GUI (dsa.msc) and pre-create the AD computer account manually and assign the "The following user or group can join this computer to the domain" to the AD service account you intend to use for deleting the AD computer account then it is assigned the correct delete permissions on the computer object EG:
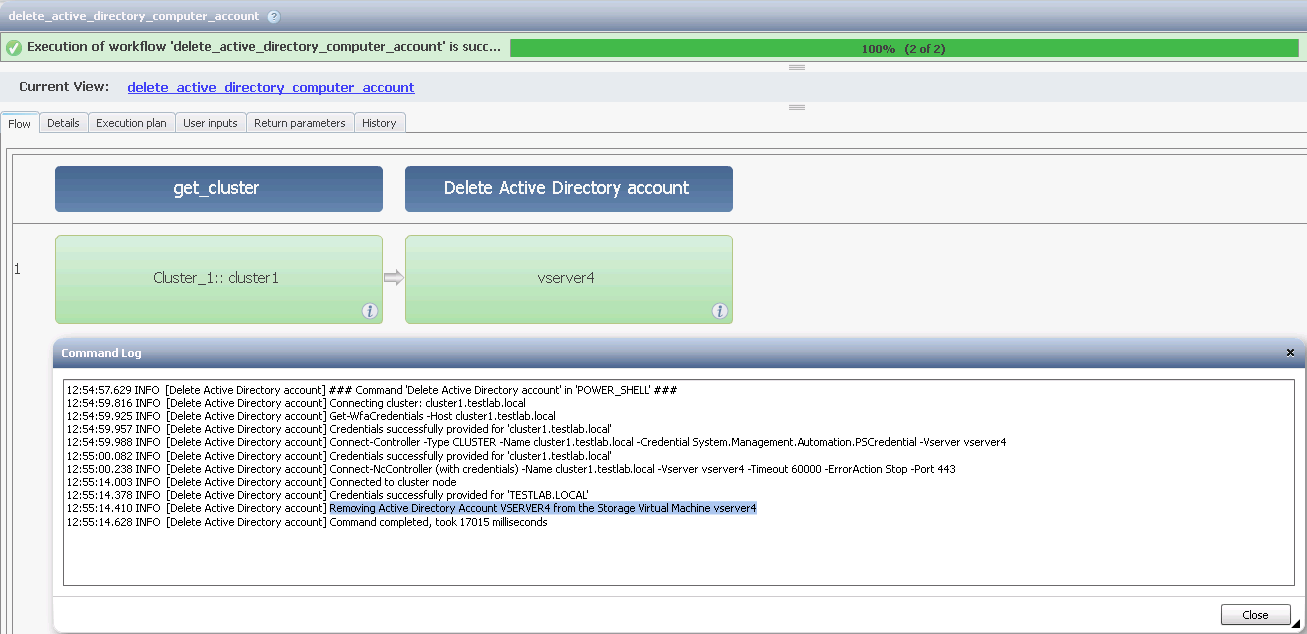
Now if i create a vserver for that computer account (re-using the computer object) when joining it to the domain i am able to use the WFA certified command "Delete Active Directory Account" to sucessfully delete the account. EG
So to summarize i think the problem is related to the Active Directory permissions on your computer object (not the WFA command).
If you like i can send you a WFA command which uses ADSI to create the computer object and assign the correct permissions.
Please let me know if you have any questions
/Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sebastiaan,
I also test this for you, if you use the WFA certified command "Setup Active Directory Account" it creates the computer object within the security context of the AD service account you've added to WFA and therefore the permissions on the computer object that is created is assigned the delete permissions required for the service account that created it. EG
You can then use the "Delete Active Directory account" command to successfully delete the computer object.
/Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matt,
Tried setting the rights on the AD object through the windows tools as suggested didn't work for me. But created the AD object through WFA and then deleting it through WFA did the trick.
Thanks.