Active IQ Unified Manager Discussions
- Home
- :
- Active IQ and AutoSupport
- :
- Active IQ Unified Manager Discussions
- :
- Re: QUESTION - Authenticating OnCMD with W2K8 AD on a RHEL box...
Active IQ Unified Manager Discussions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
QUESTION - Authenticating OnCMD with W2K8 AD on a RHEL box...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello ... I want to start a thread on a specific configuration a customer is running and having difficulty making it work.
With the information I have ( and lets us assume that all versions are current and supported ) ... a client has a RHEL system hosting OnCommand 5.X. The RHEL host itself is configured to authenticate with the W2K8 domain controller and our admins can log in ( ex: esynodinos ) with a simple user name and pass their domain password just fine. With OnCommand this is not the case. A user by the name of esynodinos is on the OnCommand admin list with Global Full Control but yet the domain password is rejected.
I have searched the forums for ideas and it may be that we have to enter LDAP credentials into OnCommand to better pass authentication requests.
We are going to ask the customer what they do to get their RHEL boxes to authenticate properly.
In the meantime, I am hoping to get some ideas from the community here.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay an update ... we may have the answer next week.
We do not have root access to the RHEL server so we will have to wait until next week but through the access we have we believe the RHEL is configured with the PAM package which allows authentication to a Windows AD system. With that in mind, through a colleague's experience, they had to set a command line only option to make DFM pass the authentication properly through PAM
the option in question is authUsePam and is only command line; once you enable it, it should just work.
However since we are in a pickle with ROOT access, no matter how we tried to fool the host system, it refused us the ability to make the change. On the actual system, our regular users can log into the host with local accounts. Those same local accounts have DFM admin user entries with GlobalFullControl but are unable to make the command line change
dfm option set authUsePam=yes
You must have the capability to perform the DFM Core Control operation in order to change these options.
Log in as a different administrator to try again.
My test instance allows me to make the change to the option. The only difference is, my test instance is a windows box and i am logged in as a domain administrator account ( domain/esynodinos )
C:\script>dfm option set authUsePam=yes
Service DFMServer: Unable to connect to Service Control Manager: 5
Changed authenticate using PAM to Yes.
You must now restart the server service:
dfm service stop server
dfm service start server
Note: Since you have chosen to use PAM authentication which is used by the
server service, you must restart the server service every time you change
the PAM configuration on this system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UPDATE - this did not work and now the curiosity is to understand if there are other linux modules out there that can configure hosts to authenticate through an active directory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
why you don,t use LDAP?
Look at this:
https://kb.netapp.com/support/index?page=content&id=1011398
It works fine and you could configure it without special permissions for root. Only a Systemaccount in th AD and two ore more groups are neccessary.
Regards
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct ... we got the AD - LDAP information and plugged them into DFM and we can authenticate with AD accounts on a Linux box through AD.
This opens up other questions, like when a OnCommand Admin user named "pete" becomes recorded as a series of contain name properties. This will be a separate thread.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Martin,
So I followed the instructions according to the kb article and I'm still having issue. These are the settings that I have in my lab environment.
[root@tkoslis01 ~]# dfm options list | grep -i ldap
ldapBaseDN ou=System,ou=Accounts,dc=tkocs,dc=prv
ldapBindDN cn=svcDFM,ou=System,ou=Accounts,dc=tkocs,dc=prv
ldapBindPass ********
ldapEnabled Yes
ldapGID memberOf
ldapMember member
ldapUGID CN
ldapUID sAMAccountName
ldapVersion 3
[root@tkoslis01 ~]# dfm ldap list
Address Port Last Use Last Failure
------------------------------------------ ------ -------------------------- --------------------------
tkosmdc01.tkocs.prv 389 2012-08-17 19:10:23.000000
tkosmdc02.tkocs.prv 389 2012-08-17 19:18:41.000000
tkosmdc03.tkocs.prv 389 2012-08-17 19:25:00.000000
And this is the error that I get:
[root@tkoslis01 ~]# dfm ldap test svcDFM <password>
Warning: Failed to bind to ldap server 'tkosmdc01.tkocs.prv' as administrator 'cn=svcDFM,ou=System,ou=Accounts,dc=tkocs,dc=prv': Invalid credentials
Warning: ldapBindDN ('cn=svcDFM,ou=System,ou=Accounts,dc=tkocs,dc=prv') and/or ldapBindPass setting may be wrong.
Error: Failed to authenticate svcDFM.
I know the username and password is correct. I've tried this with a Linux system configured with Winbind authentication working and without. Not sure what I need to do and have been checking posts to see where I'm going wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
After looking at ldap setting I can guess that you are using active directory LDAP server. You are getting this error because option value for below fields are not setting correctly.
ldapBindDN cn=svcDFM,ou=System,ou=Accounts,dc=tkocs,dc=prv
ldapBindPass ********
Normal, in Ad server we create a user under "Users" directory, so in your case "ldapBindDN" field's value should be "cn=svcDFM,cn=Users,ou=System,ou=Accounts,dc=tkocs,dc=prv".
So, below option value should be
ldapBindDN cn=svcDFM,cn=Users,ou=System,ou=Accounts,dc=tkocs,dc=prv
ldapBindPass password of "svcDFM"
Also, you can bind the LDAP server with different domain user, the user that is created when you build the AD setup.
Exp: I have Administrator user in BARD_QA domain, so my LDAP setting is
[root@shoemake-rhel ~]# dfm option list | grep -i ldap
ldapBaseDN dc=bard,dc=netapp,dc=com
ldapBindDN BARD_QA\Administrator
ldapBindPass ********
ldapEnabled Yes
ldapGID memberOf
ldapMember member
ldapUGID CN
ldapUID sAMAccountName
ldapVersion 3
[root@shoemake-rhel ~]# dfm ldap test ldap_user ******
Authentication succeeded.
Username: CN=ldap_user,CN=Users,DC=bard,DC=netapp,DC=com
Name: CN=ldap_user,CN=Users,DC=bard,DC=netapp,DC=com
Name: memberOf=CN=hamlet_group,CN=Users,DC=bard,DC=netapp,DC=com
Name: CN=hamlet_group,CN=Users,DC=bard,DC=netapp,DC=com
[root@shoemake-rhel ~]# dfm ldap find ldap_user
Username Full Name
------------ ----------------------------------------------------------------
ldap_user CN=ldap_user,CN=Users,DC=bard,DC=netapp,DC=com
[root@shoemake-rhel ~]#
Please first search the user with "dfm ldap find <user_name>" command if this is success then you can user "dfm ldap test " command.
Please let me know for any further assignment
Regards,
Gireesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gireesh,
My CN is correct as that account is in the System OU, which is in the Accounts OU in my tkocs.prv domain. The CN=Users is the default area for user accounts if you are not maintaining a OU structure that is different from default. In either case, I've tried it with an account in CN=Users and got the same error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do I need to have Winbind authentication enabled on this Linux system?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok I got it to work finally. It turned out that my DN for the account svcDFM was wrong. I created a new account in CN=Users and tested with that and everything worked. I am modifying to get it for the exact BaseDN that I want all lookups to occur in.
[root@tkoslis01 ~]# dfm ldap list
Address Port Last Use Last Failure
------------------------------------------ ------ -------------------------- --------------------------
tkosmdc01.tkocs.prv 389 2012-08-18 07:15:44.000000
tkosmdc02.tkocs.prv 389 2012-08-18 07:17:50.000000
tkosmdc03.tkocs.prv 389 2012-08-18 07:18:32.000000
[root@tkoslis01 ~]# dfm option list | grep -i ldap
ldapBaseDN ou=Users,ou=Accounts,dc=tkocs,dc=prv
ldapBindDN CN=svcDFM,OU=System,OU=Accounts,DC=tkocs,DC=prv
ldapBindPass ********
ldapEnabled Yes
ldapGID memberOf
ldapMember member
ldapUGID CN
ldapUID sAMAccountName
ldapVersion 3
[root@tkoslis01 ~]# dfm ldap find andreclark
Username Full Name
------------ ----------------------------------------------------------------
andreclark CN=Andre M. Clark,OU=Users,OU=Accounts,DC=tkocs,DC=prv
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
You have three LDAP servers, "dfm ldap find/test" command first try to search the user in first LDAP server.
So, do you have ldap user "svcDFM" in "tkosmdc01.tkocs.prv" server ..?
Regards,
Gireesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Emanuel,
These are procedures I put together to allow a Linux based installation of NetApp OnCommand Unified Manager (Operations Manager/Data Fabric Manager) authenticate against Microsoft Active Directory. NetApp does have this documented in Knowledgebase article 1011398 however I found it not as complete as it could be.
One important thing to note is that you can configure this to work without having the hosting Linux system using Pluggable Authentication Modules (PAM) or Samba Winbind.
Requirements
- Microsoft Active Directory 2003 or higher
- NetApp OnCommand Unified Manager/Operations Manager/DFM
- NetApp recommended Linux distribution
Helpful Utility
- Active Directory Explorer (http://technet.microsoft.com/en-us/sysinternals/bb963907.aspx) - although this is not a requirement I highly recommend using it as it will help you get the correct Distinguished Name (DN) that will be needed for the LDAP setup.
Steps
- Outside of the AD configuration, I made all of my UM/OM/DFM changes from the CLI. You can make the configuration changes from the GUI (Setup > Options > LDAP).
- Create an account in AD that will be used for the LDAP lookups (i.e. LDAPLkUp). This needs to be a regular account and can be defined with no logon access. Specify a password that meets the required security requirements, however please note that some characters (&%$ etc.) do have unique purposes in Linux so I would avoid these characters. Additionally, make a note of where in AD you are creating this account as you will need this information later.
I created account "LDAPLkUp" in the tkocs.prv> Accounts> System Organization Unit (OU)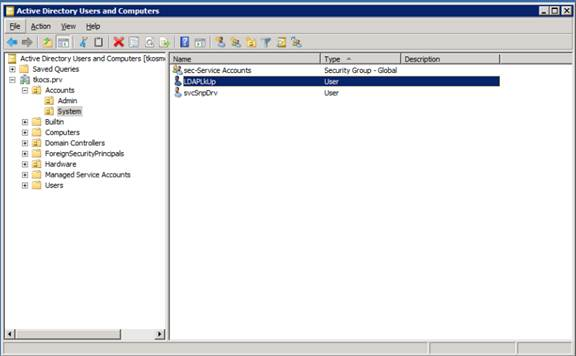
- Using Active Directory Explorer, make note of the of the DN of the location that you want the LDAP queries to occur and the DN of the account that you will be using for the lookups.
All of the groups and accounts I'm using are in TKOCS.PRV> Accounts OU. Note the DN is the information in the Path field of AD Explorer.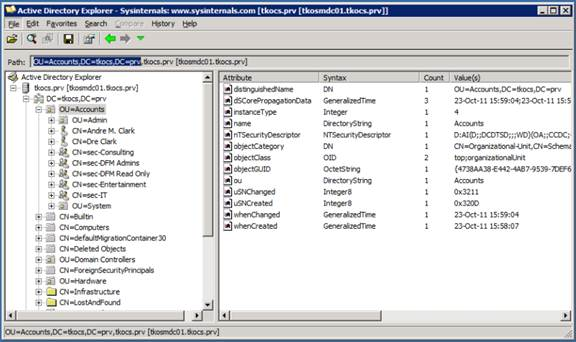

- Now that you have this information, you are ready to make the configuration changes in UM. From the CLI of the UM server, update the following items:
- dfm ldap add [-P <default-port>] <address>[:<port>]
This is where you set your ldap server(s) and port. The default port for LDAP is 389 so there's no need to specify it. You want to use the LDAP/AD server(s) that are in the same site/location as the UM server.
dfm ldap add tkosmdc01.tkocs.prv tkosmdc02.tkocs.prv tkosmdc03.tkocs.prv - dfm ldap template netscape
- dfm option set ldapBaseDN=OU=Accounts,DC=tkocs,DC=prv
This is the location where you UM to perform the queries. - dfm option set ldapBindDN=CN=LDAPLkUp,OU=System,OU=Accounts,DC=tkocs,DC=prv
This is the account that will perform the lookups - dfm options set ldapBindPass= **************
Set this option to the password of your account in the previous step - dfm options set ldapGID=memberOf
- dfm options set ldapMember=member
- dfm options set ldapUGID=CN
- dfm options set ldapUID=sAMAccountName
- dfm options set ldapVersion=3
- dfm options set ldapEnabled=Yes
- dfm ldap add [-P <default-port>] <address>[:<port>]
- Verify all of your changes
# dfm ldap list
Address Port Last Use
------------------------------------------ ------ --------------------------
tkosmdc01.tkocs.prv 389 2012-08-19 17:14:53.000000
tkosmdc02.tkocs.prv 389 2012-08-19 17:14:53.000000
tkosmdc03.tkocs.prv 389 2012-08-19 17:14:53.000000
# dfm option list | grep -i ldap
ldapBaseDN OU=Accounts,DC=tkocs,DC=prv
ldapBindDN CN=LDAPLkUp,OU=System,OU=Accounts,DC=tkocs,DC=prv
ldapBindPass ********
ldapEnabled Yes
ldapGID memberOf
ldapMember member
ldapUGID CN
ldapUID sAMAccountName
ldapVersion 3 - Perform a query lookup. If everything is configured correctly, you should see the following
# dfm ldap find andreclark
Username Full Name
------------ ----------------------------------------------------------------
andreclark CN=Andre M. Clark,OU=Accounts,DC=tkocs,DC=prv
- You are now ready to add LDAP user accounts and/or groups to the UM server. Because you are doing this all based on LDAP, you have to enter in everything via the DN (CLI or GUI).
# dfm user add "CN=Andre M. Clark,OU=Accounts,DC=tkocs,DC=prv"
# dfm user add "CN=sec-DFM Read Only,OU=Accounts,DC=tkocs,DC=prv"
# dfm user list
Id Administrator Email Pager
----- ---------------------- ------------------------ ------------------------
132 CN=Andre M. Clark,OU=Accounts,DC=tkocs,DC=prv
131 CN=sec-DFM Admins,OU=Accounts,DC=tkocs,DC=prv
130 CN=sec-DFM Read Only,OU=Accounts,DC=tkocs,DC=prv
34 Everyone
35 root
The first is an example of adding a single user; the second is an example of adding a security group.
